Abstract:
Install Virtualbox in computer system, in which to install Kali Linux, then try wireshark, nmap and crunch application. It shows a lot of security tools can be implemented correctly in Virtualbox.
Methods:
Go to virtualbox page to download the virtual 5.2.18 version, then install it based on wizard.
Search “kali OVA”, then go to official kali linux download page, select the “Kali Linux 64 bit Vbox”, click “offensive security download page” icon to select “Kali Linux 64 bit Ova” which is for Virtualbox, download it.
Open Virtual box,click “file” button then select “import application”, input the “kali 2018.3 ova” into the frame, then select the fold where the “kali linux 64 bit” you have download before, then open it.
Select the “OS Redhat 64 bit”, choose all other items as defaults, such as sound card, network adapter card etc, then click “import”. Waiting a couple minutes to finish installing. After installation, you can see “kali 2018.3” icon on the Virtualbox panel.
Double click the “kali 2018.3”, it will start to boot, just taking defaults. Input the username “root” and password “toor” to log in Kali.
Click the top panel of Kali, select firefox browser to input “google” to create some packets, then click No.9 sniffing and spoofing to select wireshark to open it. Ignore the Lua message,then click the “eth0”.
Using Kali terminal to input command “ping 192.168.0.1” to connect router.
Check the wireshark, stop it and capture the packets.
Input “ifconfig eth0” command in Kali terminal, get the information of ip address 10.2.0.15, then go to wireshark to capture the packets. Input the “ICMP” into wireshark frame to observe just ICMP packets. then save it and get a screenshot.
In Kali machine to click nmap application. Then in terminal command line to input “nmap -v -A scanme.nmap.org” command to do OS detection and version detection, script detection of “scanme.nmap.org”, meanwhile in wireshark to start a new packet capture. using filter to limit the packets both to and from 45.33.32.156 in and out this virtual machine. Get a screenshot from wireshark.
In Kali click the “crunch” application, which can create a wordlist based on your criteria, then you can use this wordlist to a file or a program.
In terminal line, input “crunch 1 2 > /tmp/wordlist” to test this application.
Results:
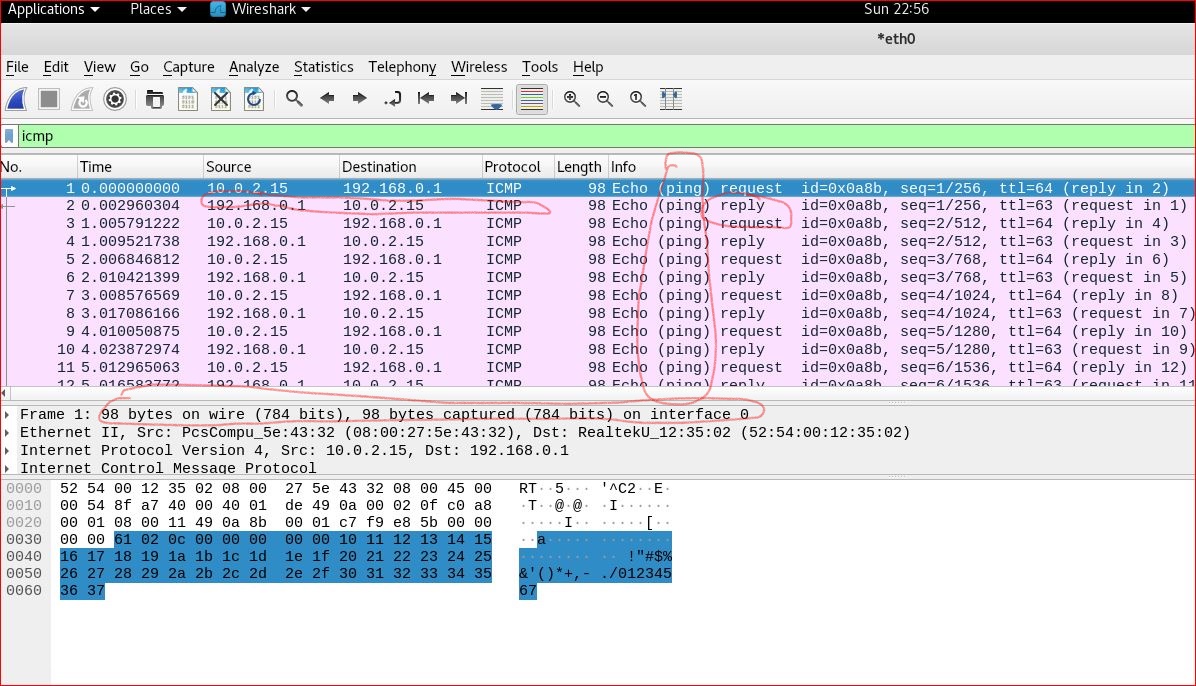
“Ping 192.168.0.1” command can get the response from router. It shows packets can successfully go through from virtual machine to out router. After paused the wireshark, narrow down to ICMP, wireshark shows there are totally 98 bytes, displayed 98 bytes, no dropped between 192.168.0.1 and 10.0.2.15.It shows the packets to and from inside and outside.
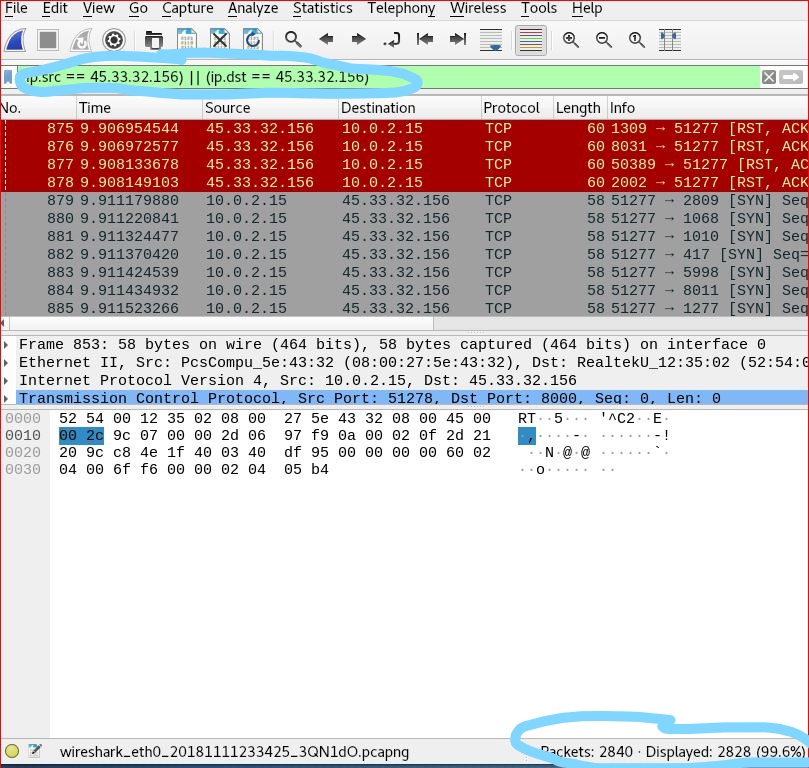
After filter the packets just between the 10.0.2.15 and 45.33.32.156 (scanme.nmap.org) it shows 99.6% displayed which are 2828 packets in the wireshark capture screenshot.It also shows using TCP protocol to visit the www.scanme.nmap.ogr successfully.
1 | crunch 1 2 > /tmp/wordlisttest |
It generated a wordlist starts from “a”, ends to “zz”, then save it as a file named “wordlisttest” in tmp folder in Kali linux.
Virtualbox is a powerful application on which a lot of machine can run. In Kali, Nmap has command line interface, which is easy to use compared to GUI interface.