Abstract:
Using Zenmap, enumerating 2 IP address to scan, Using Wireshark to observe the TCP handshake process when enumerating 2 IP addresses with Zenmap.
Introduction:
Scan 2 IP with Zenmap and use Wireshark to observe the TCP handshake.
Methods:
Go to nmap page to download zenmap application.
Open Wireshark to see the Wi_Fi wiggling wave, it shows capturing the packets, then click it.
Open Zenmap, input first IP address 192.168.227.187 into “target” frame, then select “quick scan” to see what will happen.
go to Wireshark to stop and save it for first IP scan.
go back to Zenmap to input other IP address into “target” frame, do quick scan again.
In Wireshark, select the source and destination IP address 192.168.0.1 to observe the captured packets, analyze the TCP handshake process.
Results:
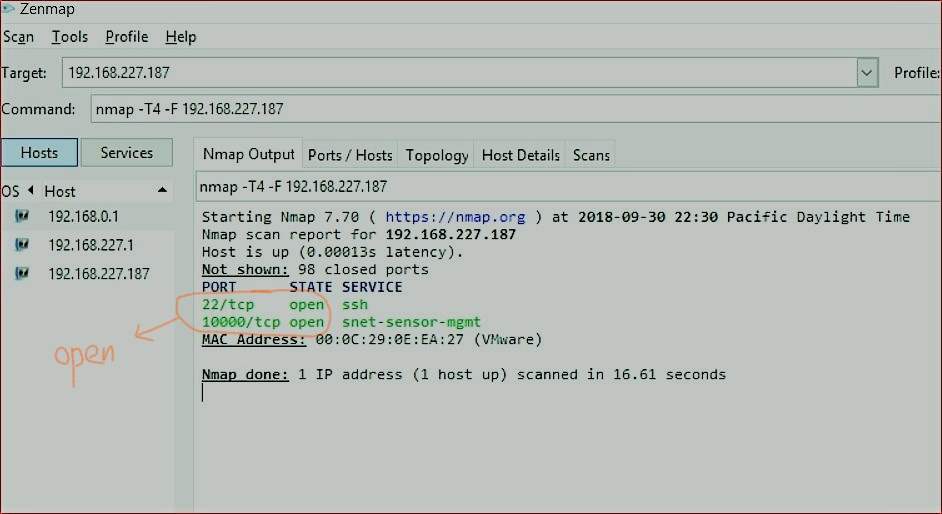
For the 192.168.227.187 address, zenmap quickly scanned 100 ports, 98 ports are closed, port 22 and port 10000 are open.
For the 192.168.0.1, Zenmap shows there are 4 ports open, they are ports 53,80, 8080, 8443.
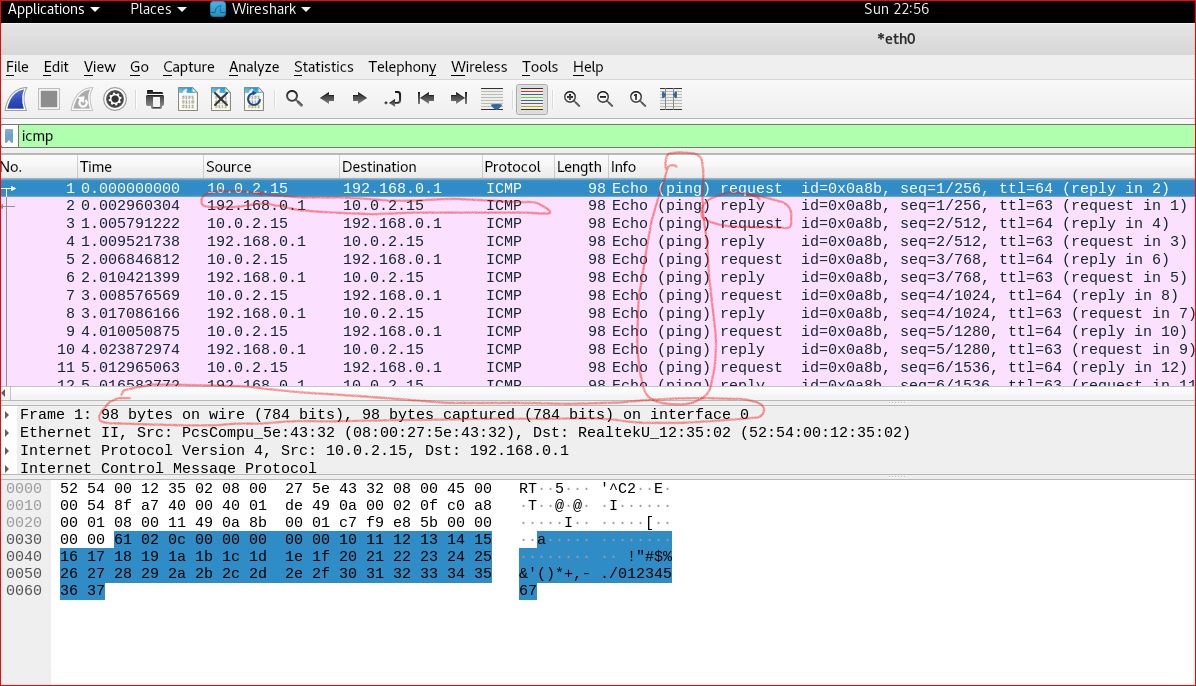
In Wireshark, observing the packets from 192.168.0.1, it shows the synchronized three way handshake.
a. from the source 192.168.0.140 sent the request to 192.168.0.1, the flag is SYN
b. from the destination 192.168.0.1 to 192.168.0.140, it acknowledges that it receives the request and at the same time, closed the socket. The flag is RST ACK.
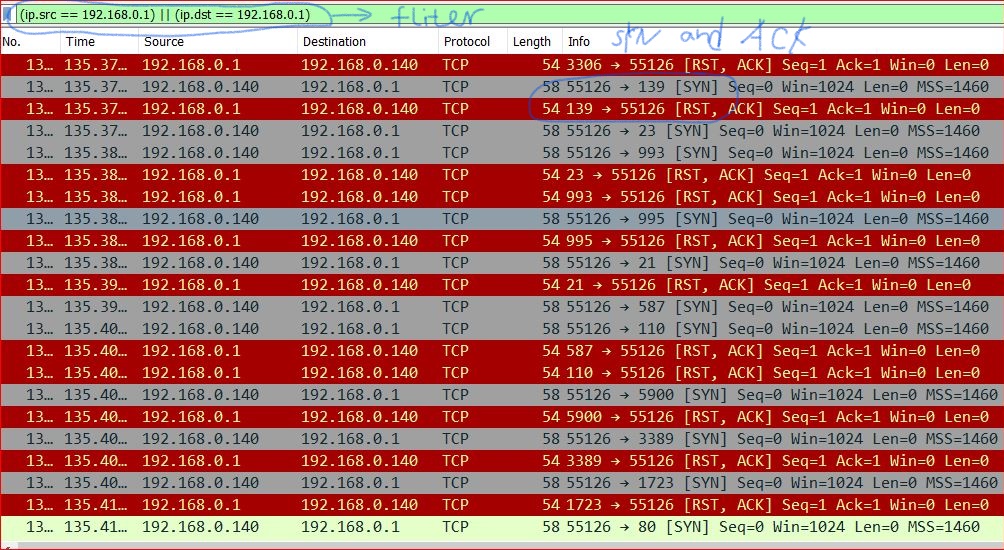
Also notice some requests from 192.168.0.140 to 192.168.0.1 didn’t get acknowledge from the destination port
Discussion:
Sometimes there is no “three” handshakes, only “two” handshakes, because the host B is going to close the sockets after it acknowledge the packets that were sent from the host A.