Clean Desk Policy:
Goal:
Establish the minimum requirements for maintaining a “clean desk” – where sensitive/critical information about employees, intellectual property, students is secure in locked areas and out of site.
Procedure:
a.Employees are required to ensure that all sensitive/confidential information in hardcopy or electronic form is secure in their work area at the end of the day and when they are expected to be gone for an extended period.
b.Computer workstations must be locked when workspace is unoccupied.
c.Computer workstations must be shut completely down at the end of the work day.
d.Any Restricted or Sensitive information must be removed from the desk and locked in a drawer when the desk is unoccupied and at the end of the work day.
e.File cabinets containing Restricted or Sensitive information must be kept closed and locked when not in use or when not attended.
f.Keys used for access to Restricted or Sensitive information must not be left at an unattended desk.
g.Laptops must be either locked with a locking cable or locked away in a drawer.
h.Passwords may not be left on sticky notes posted on or under a computer, nor may they be left written down in an accessible location.
i.Printouts containing Restricted or Sensitive information should be immediately removed from the printer.
j.Upon disposal Restricted and/or Sensitive documents should be shredded in the official shredder bins or placed in the lock confidential disposal bins.
k.Whiteboards containing Restricted and/or Sensitive information should be erased.
l.Lock away portable computing devices such as laptops and tablets.
m.Treat mass storage devices such as CDROM, DVD or USB drives as sensitive and secure them in a locked drawer.
Password Policy:
Goal:
Passwords are a critical component of information security and serve to protect user accounts; however, a poorly constructed password may result in the compromise of individual systems, data, or network. This policy provides best practices for creating secure passwords.
Procedure:
a.Strong passwords are long, the more characters you have the stronger the password.
b. We recommend a minimum of 14 characters in your password.
c. We highly encourage the use of passphrases, encourage the use of ‘password manager’ software,passwords made up of multiple words.
Email Policy:
Goal:
The purpose of this policy is to ensure the proper use of email system and make users aware of Chabot College deems as acceptable and unacceptable use of its email system. This policy outlines the minimum requirements for use of email within Chabot College Network.
Procedure:
a. All use of email must be consistent with Chabot College policies and procedures of ethical conduct, safety, compliance with applicable laws and proper business practices.
b. Email account should be used primarily for Chabot College business-related purposes; personal communication is permitted on a limited basis.
c. All Chabot College data contained within an email message or an attachment must be secured according to the Data Protection Standard.
d.The Chabot College email system shall not to be used for the creation or distribution of any disruptive or offensive messages, including offensive comments about race, gender, hair color, disabilities, age, sexual orientation, pornography, religious beliefs and practice, political beliefs, or national origin.
Related Standards, Policies and Processes:
Data Protection Standard
End User Encryption Key Protection Policy:
Goal:
This policy outlines the requirements for protecting encryption keys that are under the control of end users. These requirements are designed to prevent unauthorized disclosure and subsequent fraudulent use. The protection methods outlined will include operational and technical controls, such as key backup procedures, encryption under a separate key and use of tamper-resistant hardware.
Procedure:
a.Keys used for secret key encryption, also called symmetric cryptography, must be protected as they are distributed to all parties that will use them. During distribution, the symmetric encryption keys must be encrypted using a stronger algorithm with a key of the longest key length for that algorithm authorized in Chabot College’s Acceptable Encryption Policy. If the keys are for the strongest algorithm, then the key must be split, each portion of the key encrypted with a different key that is the longest key length authorized and each encrypted portion is transmitted using different transmission mechanisms. The goal is to provide more stringent protection to the key than the data that is encrypted with that encryption key.
b.Public key cryptography, or asymmetric cryptography, uses public-private key pairs. The public key is passed to the certificate authority to be included in the digital certificate issued to the end user. The digital certificate is available to everyone once it issued. The private key should only be available to the end user to whom the corresponding digital certificate is issued.
c.Hardware tokens storing encryption keys will be treated as sensitive equipment, as described in Chabot College’s Physical Security policy. In addition, all hardware tokens, smartcards, USB tokens, etc.will not be stored or left connected to any end user’s computer when not in use. For end users traveling with hardware tokens, they will not be stored or carried in the same container or bag as any computer.
d.All PINs, passwords or passphrases used to protect encryption keys must meet complexity and length requirements described in Chabot College’s Password Policy.
e.The Infosec team will verify compliance to this policy through various methods, including but not limited to, periodic walkthroughs, video monitoring, business tool reports, internal and external audits, and feedback to the policy owner.
Related Standards, Policies and Processes:
a.Password Policy
b.Encryption Policy
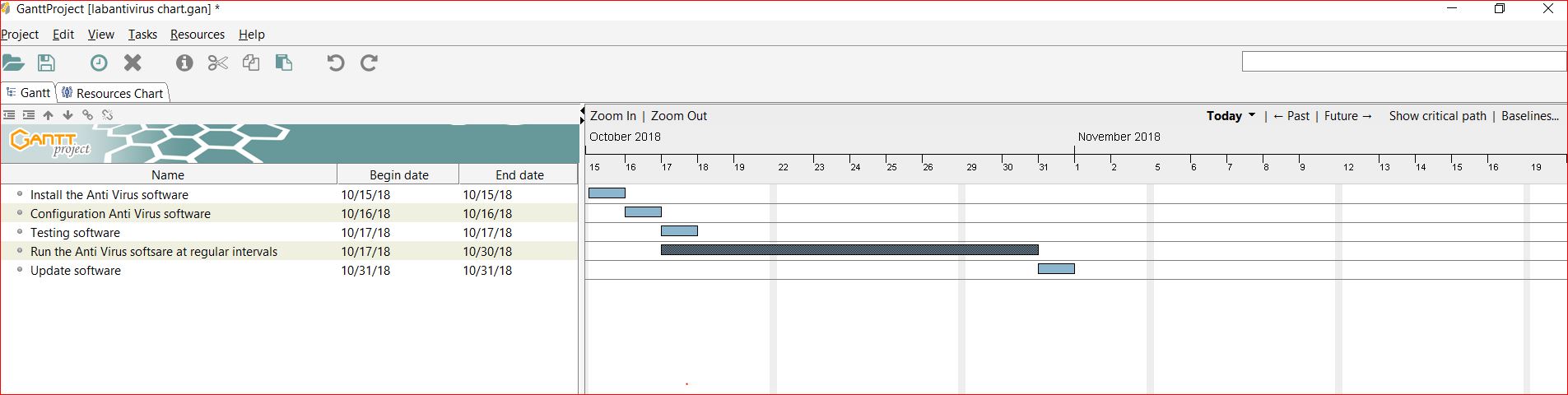
Lab Anti-Virus Policy:
Goal:
To ensure effective virus detection and prevention in Chabot College lab.
Procedure:
a. All Chabot College PC-based lab computers must have Chabot College’s standard, supported anti-virus software installed and scheduled to run at regular intervals. In addition, the anti-virus software and the virus pattern files must be kept up-to-date. b.Virus-infected computers must be removed from the network until they are verified as virus-free.
b.Lab Admins/Lab Managers are responsible for creating procedures that ensure anti-virus software is run at regular intervals, and computers are verified as virus-free. d.Any activities with the intention to create and/or distribute malicious programs into Chabot College’s networks (e.g., viruses, worms, Trojan horses, e-mail bombs, etc.) are prohibited, in accordance with the Acceptable Use Policy.
Related Standards, Policies and Processes:
•Acceptable Use Policy
•Anti-Virus Recommended Processes
The CmapTools Mind:
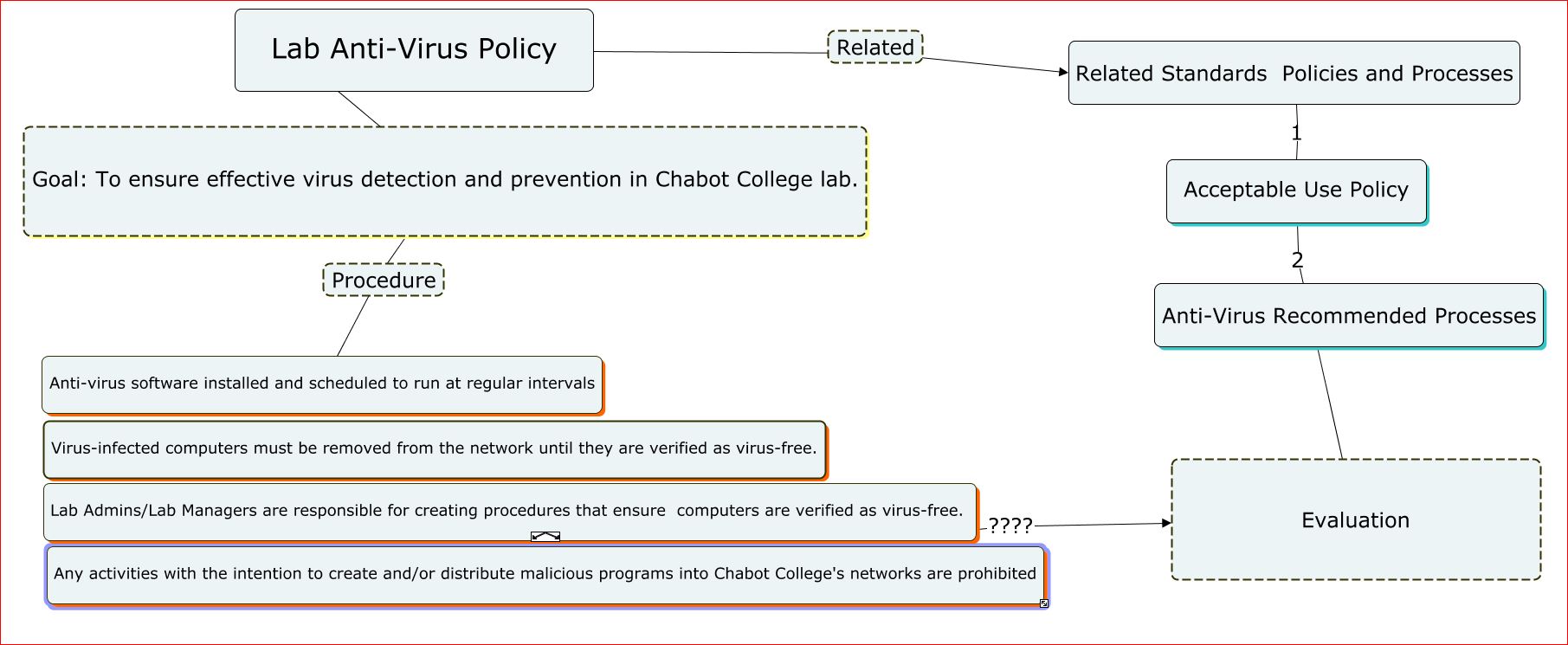
Ganttproject timeline: